APC Information Systems Security
Putting information systems security first means organization and business privacy and protection of critical data are paramount. Web sites and information systems are designed, developed, and managed to match organizational goals and objectives, comply with laws and regulations, and match industry best practices and standards.
Frameworks
Using organizational policies and guidelines is most often achieved best when adopting security frameworks and regulations with system operations. Three main frameworks exist which help guide organizations' system security and best practices: COBIT, ISO/IEC ISO 27001, and NIST SP 800 53. Together, these three frameworks help guide information systems security and services.
Industry Insights
Many different security channels and sources exist to stay abreast with things going on in the security industry. Full disclosure mailing lists help provide notices of emerging threats, zero-day exploits, and various news in different sections of the information security world: Full Disclosure, Security Lists, and Security Focus.
OWASP is an extremely valuable hub of information and insights into the security industry. SANS provides training and educational resources for security research. ISACA, ISO, and IEEE all provided an incredible collection of advice, best practices, and standards for developing secure and compliant information systems.
Exploit and vulnerability databases helps reveal weaknesses in systems and software or hardware which needs to be upgraded, hardened, and secured: Exploit DB, CVE, and NVD. US-CERT and FBI Cyber Unit also have some great insights, news, tips, and alerts to security events around the United States and the world.
PCI-DSS Compliance
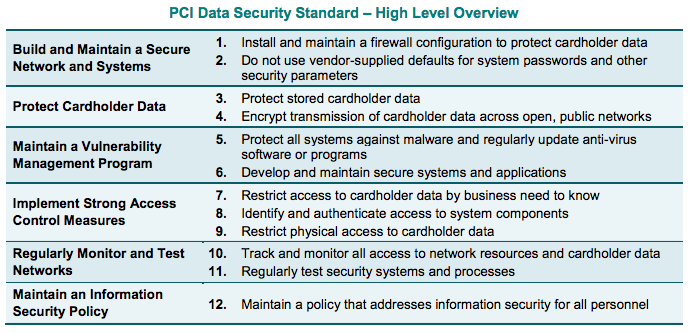 PCI-DSS applies to all businesses and organizations which process cardholder data (CHD). To reduce liability and exposure to risk of fines, information systems which process CHD must follow the PCI-DSS requirements in these main categories:
PCI-DSS applies to all businesses and organizations which process cardholder data (CHD). To reduce liability and exposure to risk of fines, information systems which process CHD must follow the PCI-DSS requirements in these main categories:
- Firewall Configuration
- Default Passwords and Hardening
- Protect Cardholder Data
- Secure Transmissions
- Vulnerability Management
- Secure Systems and Applications
- Principle of Need to Know
- Secure Authentication
- Secure Physical Access
- Track and Monitor
- Information Security Policy
HIPAA Compliance
HIPAA applies to all businesses and organizations which hold electronic protected health information (ePHI). Most businesses acquire or transact some form of ePHI, and become subject to HIPAA regulations, fines, and punishments for not treating ePHI properly. Following HIPAA guidelines, security best practices, and performing proper system security auditing will help reduce liability. Encryption, firewalls, disaster recovery, system hardening, security policies, controls, and having the right documents in place are great first steps to becoming HIPAA compliant.
Information Systems Security Services
Need help? APC can help facilitate compliance and certification for your business or organization, perform security auditing, and/or establish proper security policies, guidelines, and procedures. Contact APC for assistance.

